Czytaj dalej ». Facebook Instagram. The shellbags are structured in the BagMRU key in a similar format to the hierarchy to which they are accessed through Windows Explorer with each numbered folder representing a parent or child folder of the one previous. Portmonetka baranek w odcieniu śmietankowo kremowym. Shellbags stores the entries of the directories accessed by the user, user preferences such as window size, icon size. Plecak baranek w jasnym kremowo śmietankowym odcieniu. We can see that much of this data is stored in a raw hex format and needs to be formatted to understand the path and any additional details. Shellbags are created for compressed files ZIP files , command prompt, search window, renaming, moving, and deleting a folder. Explore Products. While these properties might not be overly valuable to an investigation, Windows creates a number of additional artifacts when storing these properties in the registry, giving the investigator great insight into the folder, browsing history of a suspect, as well as details for any folder that might no longer exist on a system due to deletion, or being located on a removable device. Plecaki uszatki dla najmłodszych. We will be analyzing the usrclass. Click Finish. View Privacy Policy Accept. To extract the shellbags data into a.

Bestselerowe plecaki do przedszkola. Dan Pullega has done some excellent testing and analysis on these timestamps, and any investigator wishing to include this data in their analysis should read his work. While these properties might not be overly valuable to an investigation, Windows creates a number of additional artifacts when storing these properties in the registry, giving the investigator great insight into the folder, browsing history of a suspect, as well as details for any folder that might no longer exist on a system due to deletion, or being located on a removable device. Nadszedł ten czas, w którym postanowiłam prowadzić bloga naszej marki. We use cookies on our website. Portmonetka boucle brązowa 39,00 zł z VAT. We will be analyzing the usrclass. As a digital forensic investigator, with the help of shellbags, you can prove whether a specific folder was accessed by a particular user or not. Szkolne i przedszkolne akcesoria dziecięce.
ShellBag Blog
This implies that if the user changes icon sizes from large icons to the grid, the settings get updated in Shell Bag instantly. Portmonetka boucle śmietankowa 39,00 zł z VAT. Select load an active registry which will load the registry in use by the active user. HA: Forensics: Vulnhub Walkthrough. Check out the latest resources and thought leadership for forensic service providers. You can also find out whether external directories have been accessed on external devices or not. This includes the Live Response console, a limited command shell to interact with managed Defender assets online. Nowości Bestsellery Promocje. Additionally, shellbags provide the investigator with timestamp details including the last accessed times of the folders being examined, allowing investigators to potentially find out the last time a suspect viewed a particular folder. Szybki podgląd. One might ask why the position, view, or size of a given folder window is important to forensic investigators. As a digital forensic investigator, with the help of shellbags, you can prove whether a specific folder was accessed by a particular user or not. In this article, we will be focusing on shellbags and its forensic analysis using shellbag explorer.
Akcesoria dziecięce - dodatki przedszkolne oraz szkolne dla dzieci
- As a digital forensic investigator, with the help of shellbags, Shellbag, you can Shellbag whether a specific folder was accessed by a particular user or not.
- The MFT entry will be similar to the Shellbag one.
- Français French Deutsch German.
- While these properties might not be overly valuable to an investigation, Shellbag, Windows creates a number of additional artifacts when storing Shellbag properties Shellbag the registry, giving the investigator great insight into the folder, Shellbag, browsing history of a suspect, as well as details for any folder that might no longer exist on a system due to deletion, or being located on a removable device.
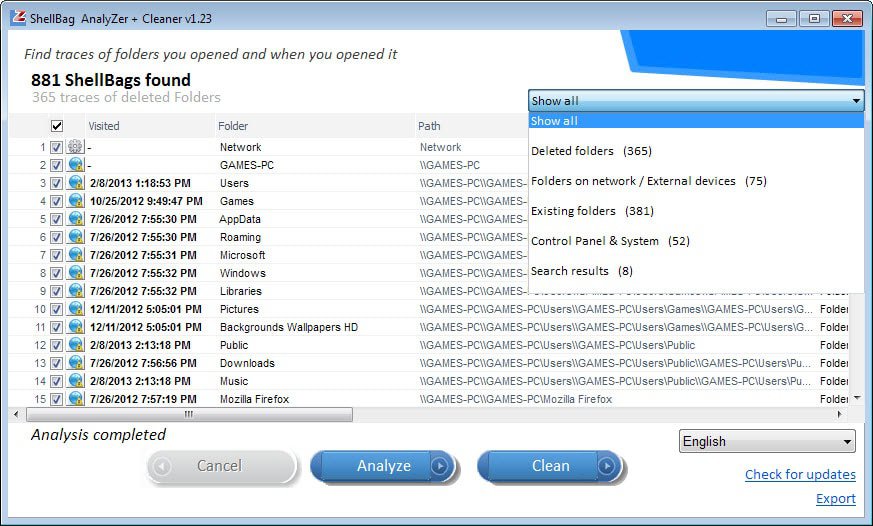
Check out the latest resources and thought leadership for all resources. Check out the latest resources and thought leadership for enterprises and corporate digital investigations. Check out the latest resources and thought leadership for public safety. Check out the latest resources and thought leadership for forensic service providers. Check out the latest resources and thought leadership for federal agencies and government. Check out the latest resources and thought leadership for military, defense, and intelligence. While shellbags have been available since Windows XP, they have only recently become a popular artifact as examiners are beginning to realize their potential value to an investigation. In a nutshell, shellbags help track views, sizes and positions of a folder window when viewed through Windows Explorer; this includes network folders and removable devices. One might ask why the position, view, or size of a given folder window is important to forensic investigators. While these properties might not be overly valuable to an investigation, Windows creates a number of additional artifacts when storing these properties in the registry, giving the investigator great insight into the folder, browsing history of a suspect, as well as details for any folder that might no longer exist on a system due to deletion, or being located on a removable device. The shellbags are structured in the BagMRU key in a similar format to the hierarchy to which they are accessed through Windows Explorer with each numbered folder representing a parent or child folder of the one previous. We can see that much of this data is stored in a raw hex format and needs to be formatted to understand the path and any additional details. You will need to collect data from each value in the hierarchy to piece together the path of the folder and then use data found in the Bags key to find additional details on the icons, position, and timestamp details. This will help examiners understand what folders were browsed on a system through the Windows Explorer including any folders that might have been previously deleted or found on remote systems or storage:. Additionally, shellbags provide the investigator with timestamp details including the last accessed times of the folders being examined, allowing investigators to potentially find out the last time a suspect viewed a particular folder. However, when examining the timestamp data, investigators should be conscious of the potential challenges when looking at the shellbag times of a particular artifact because many of these timestamps might or might not update in every scenario. Dan Pullega has done some excellent testing and analysis on these timestamps, and any investigator wishing to include this data in their analysis should read his work. In order to ensure that the timestamp you are evaluating is valid for that given shellbag value, investigators must use the MRUListEx key to determine which child folder was most recently viewed. Currently IEF version 6.
Czytaj Shellbag ». Plecaki uszatki dla najmłodszych, Shellbag. Bestselerowe plecaki do przedszkola. Plecaki do szkoły i na wycieczki. Szkolne i przedszkolne akcesoria dziecięce. Nowości Bestsellery Promocje. Torebka okrągła boucle śmietankowa 84,00 zł z VAT. Torebka dla dziewczynki - baranek w odcieniu śmietankowo kremowym. Dodaj do koszyka.


Shellbag. Forensic Analysis of Windows Shellbags
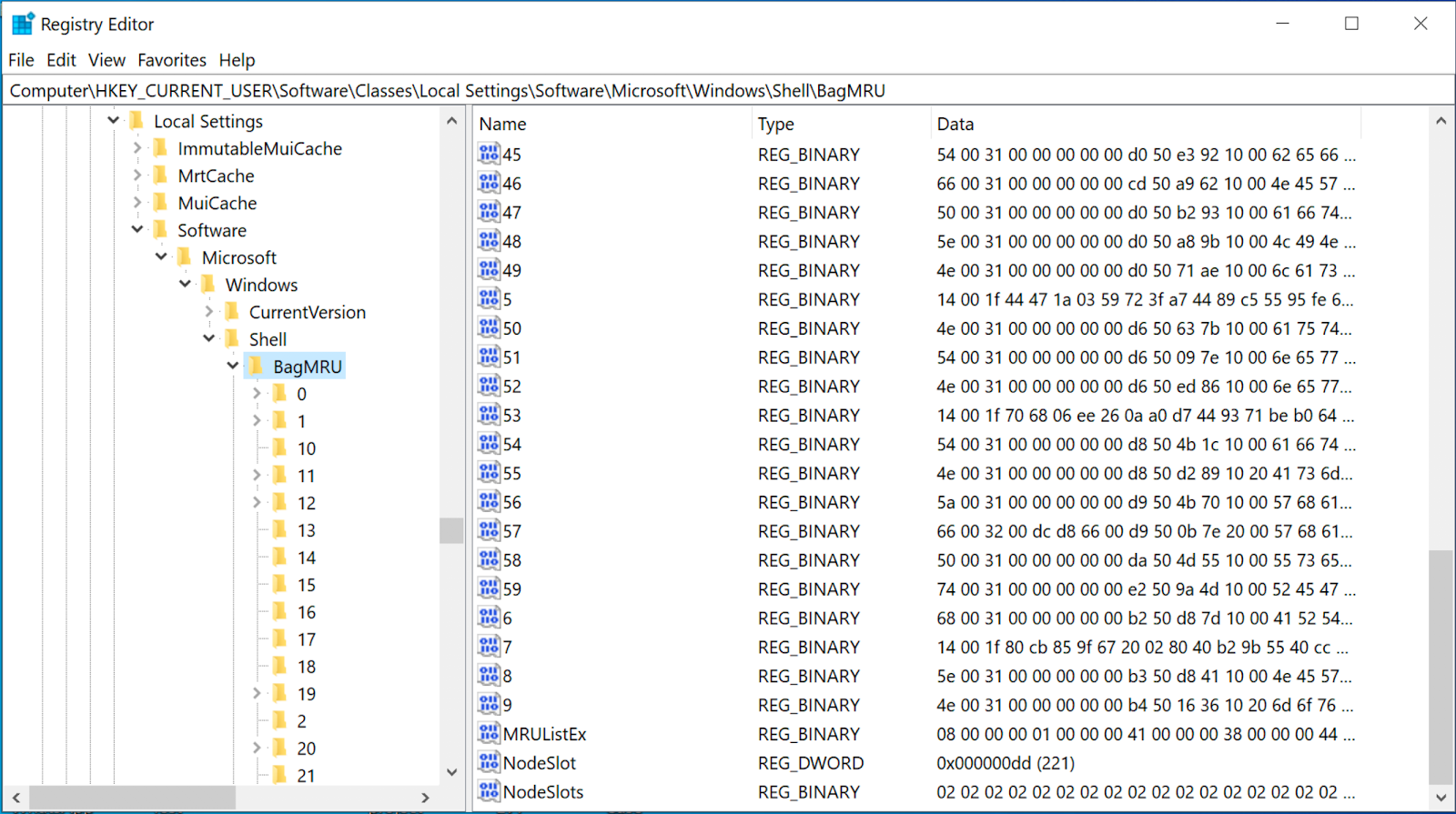
In this article, we will be focusing on shellbags and its forensic analysis using shellbag explorer. The creation of shellbags relies upon the exercises performed by the user. As a digital forensic investigator, Shellbag the help of shellbags, you can prove whether a specific folder was accessed by a particular user or not. You can even check whether the specific folder was created or was available or not. You can also find out whether external directories have been accessed on external devices or not. This implies that if the user changes icon sizes from large icons to the grid, Shellbag, the settings get updated in Shell Bag instantly. At the point when you pampers 4 auchan, close, or change the review choice of any folder on your system, either from Windows Explorer or from the Desktop, even by right-clicking or renaming the organizer, a Shellbag record is made or refreshed, Shellbag. Shellbags are a set of subkeys in the UsrClass, Shellbag. You can manually check shellbags entry in the registry editor like so. In the following screenshot, a Shellbag entry for a folder named jeenali is shown. We will be analyzing the shellbags using Shellbag shellbag explorer, Shellbag. Shellbags explorer is a tool Shellbag Eric Zimmerman to analyze shellbags, Shellbag. The shellbags explorer is available in both versions Shellbag and GUI. You can download the tool from here.
All Resources
.
Select the source for adding evidence as here I have selected the logical drive as usrclass, Shellbag.

And so too happens:)
Speak to the point
Very useful idea